IoT Deployment: Best Practices for Enterprise Use
When a project gets to the deployment stage, it is common to see deadlines getting tight, budgets getting squeezed, and unexpected challenges popping up forcing businesses to address them "on the go". Although the culmination of IoT development is already over, the control software has been tested and is ready for launch, there is still an outcome in front. The IoT deployment processes directly impact whether the application will work in the specific environment and whether it finally will achieve the business goals. It’s crucial to approach this stage with a cool head.
According to various estimates, 40 to 75% of IoT projects fail at the deployment stage. Nevertheless, it does not reduce global attempts to master IoT-related technologies as well as high interest in IoT development in general. Thus, substantial experience has been accumulated, which can help sort out dos and don’ts regarding IoT networking in various environments. PSA has gathered some of the best business and DevOps practices to help you kick off your IoT successfully. With these practices, you'll have a smooth and seamless experience as you launch your IoT solution. Move on to learn how to strategize, set priorities, prepare, and execute this phase on the field.
IoT Deployment: Features
When you launch enterprise IoT solutions, you're committing to delivering their fundamental values. Thus, continuous data collection and transfer, availability of the devices, and transparency for the whole process have to be provided unconditionally. At the stage of IoT deployment, you can both amplify and violate these values.
When it comes to creating a sustainable IoT environment, every enterprise, whether it's an automotive assembly shop or smart farm, needs to overcome deployment challenges related to the following common features:
-
Numerous diversified and distributed devices
-
Devices and systems with no internet access provided; legacy equipment
-
Complex and multi-signal environments; hard-to-reach places
-
The need for continuous data transfer 100% time for particular cases (IIoT, Healthcare, etc.)
-
Impossibility to fully predict the system’s behavior due to interaction with the real world
-
Potential scalability of IoT device network
-
Vulnerability of end-points and large attack surfaces
As the scale of IoT deployment continues to grow, we're starting to see the impact of these factors becoming more and more. The complex IoT environments often require more decentralized networks not to create bottlenecks in data transfer and simplify business process management. Generally speaking, IoT deployment follows the general framework of a successful IoT project, keeping a strict focus on the main business goal and rigorous strategic planning. When planning a deployment, you should study in detail the market offerings, the operating environment, and legal issues to comply with all requirements. It is also helpful here to be a bit of a forecaster as well so that you can adjust your environment to account for possible future changes.
IoT Deployment: Common Models
There are plenty of architectures that apply to the EIoT environment, but they all can be categorized into direct and indirect connectivity opportunities. Within the first type, things are connected directly to the cloud or local server, while the second involves intermediate devices for things to communicate with the server. The scale of IoT deployment is the most common factor to be guided by when choosing a model. It’s one thing for a smart home, greenhouse, or lab, and quite another for a production with a large number of management levels. Take a look at the figure below.
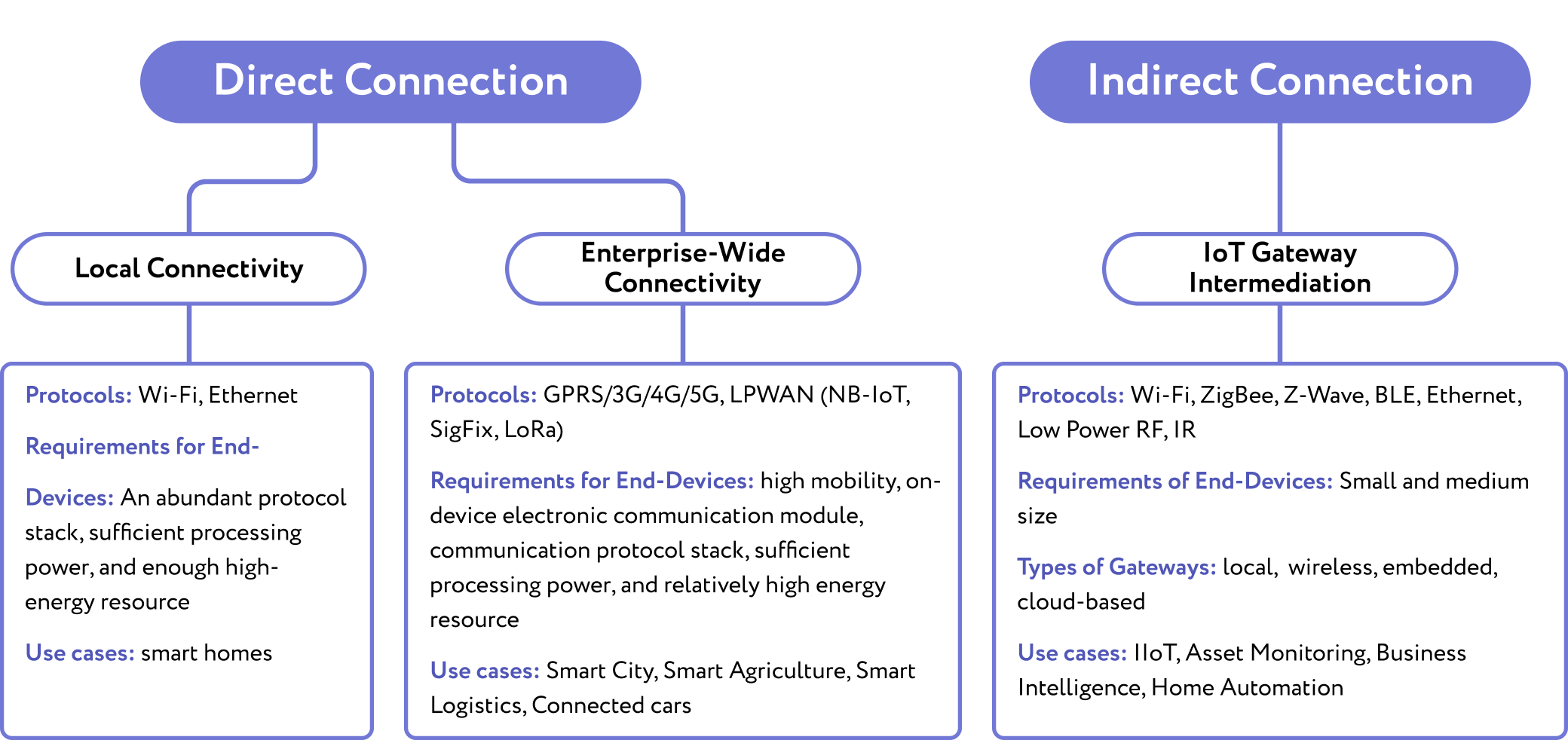
Tips on IoT Deployment: How to Mitigate Challenges
The goal of the IoT deployment is to build a reliable, scalable, and secure network that requires as little maintenance effort as possible. Below we have revealed comprehensive practices to help you follow the right path when deploying the IoT ecosystem
Take Enough Time for PRE-Stage of IoT Deployment
When approached correctly, research planning and PoC steps are the most time-consuming through their fundamental nature. This allows not only to assess the risks but also to identify and justify investments properly. Since deployment costs do not pay off, it’s helpful to show how the selected deployment model, technologies, and strategy support the overall goal of the IoT introduction project. The planning stage can be considered completed when you set goals, identify metrics, assign responsible teams, define use cases, and evaluate technical resources and business processes.
As for Proof of Concept, it is worth taking additional months or even years to implement it, since neglecting the pilot could cost you the project. Several moments are often missed while IoT testing. If you plan to deploy your IoT solution in crowded areas, test how the devices perform in congested radio conditions. An accurate risk assessment will provide insights on how to maintain wireless performance with unintended signals. If your case requires 100% real-time operation, such as IoT solutions for manufacturing or medical IoT, pay special attention to the accessibility of devices and adjust the power modes. We recommend creating or purchasing devices initially flexible to evaluate different connectivity options at the stage of testing.
Only when you are sure that you have a strong business case, you have a backup plan in case of connectivity failures, and human resources are agreed upon for this, you can proceed with IoT deployment.
Make Sure Your Legacy Be Upgraded Properly for IoT Deployment
The greatest concerns of IoT deployment usually come with transforming entire legacy production systems to IoT. Typically, such systems involve powerful equipment that has to be upgraded to meet the requirements of continuous multiple data collection, reliable connectivity, cloud connection, real-time operations through the internet, and remote control. For the needs of Digital Transformation, updates must be approached comprehensively. That is, when deploying IoT in an already existing production system, controlled, for example, by RTU, VFD, PLC, etc., updates have to be implemented at each production layer.
When it comes to achieving IoT success for legacy systems, the key often lies in the well established interactions between IoT and SCADA. When the IoT and SCADA-generated data complement each other, it can be fruitfully analyzed in the common analytical center. Since legacy database management systems simply cannot manage a substantial volume of data and adapt to the growth of connected devices, they should be supported by IoT edge devices integrated into an ecosystem.
Distributed loads and reliable transition protocols will help minimize latency issues in the future, simplifying system maintenance. To empower legacy systems, find a balance between centralized and distributed compute nodes. It is worth placing advanced analytics applications in the cloud, while real-time operations to be run at the edge. The optimal solution here would be to enable one or more gateways for a group of machines, connecting them directly via a wireless modem. To provide fast and reliable data transfer, it would be better to install a transmitter for the data transfer to a central IoT gateway, which then sends it to the cloud.
Consider the Future Applications for the IoT Deployment
To be prepared for the rapidly changing business and technological landscape, it is worth providing flexibility, interoperability, and scalability potential for IoT systems and their components. It will help adjust for various unpredicted cases, from computing power boosts to legislative amendments. The design of devices is recommended to be unified avoiding multiple versions.
Interoperability also increases opportunities for global IoT deployment. It allows devices to be connected to any network and adapt to changes while remaining accessible. It's a good idea to take this into consideration, especially when working with mobile networks. External factors like legislation issues and the range of vendors and their offerings can have an influence in this area. Most likely, you will not be able to achieve 100% coverage in this case. Based on what was mentioned earlier, its crucial to conduct further research and carefully consider alternative options in this case.
Scalability is the second crucial point. Again, we talk about strategy improvements first to predict future scalability. It relates to devices that should have enough computing power, energy, and memory resources to support increased loads. If you foresee segmented architecture in advance, as well as the opportunity to seamlessly add nodes, the scalability will be performed more rapidly. By implementing various technologies for data storing, you make the process of scalability more organized. Then, consider the approach for devices with constrained bandwidth, which may become a considerable bottleneck when scaling. One more is a platform to be capable of adding new types of devices and monitoring parameters.
Provide Transparent Data Monitoring and End-Point Management
In complex and distributed IoT environments, it’s vital to maintain their predictability. Tools for setting up and monitoring an IoT network solve the problem of maintaining thousands of interconnected IoT devices with limited physical access. As a rule, the server application allows you to configure real-time monitoring, notifying, and reporting according to specified parameters for all interested parties.
By deploying such applications, you can leverage the following benefits:
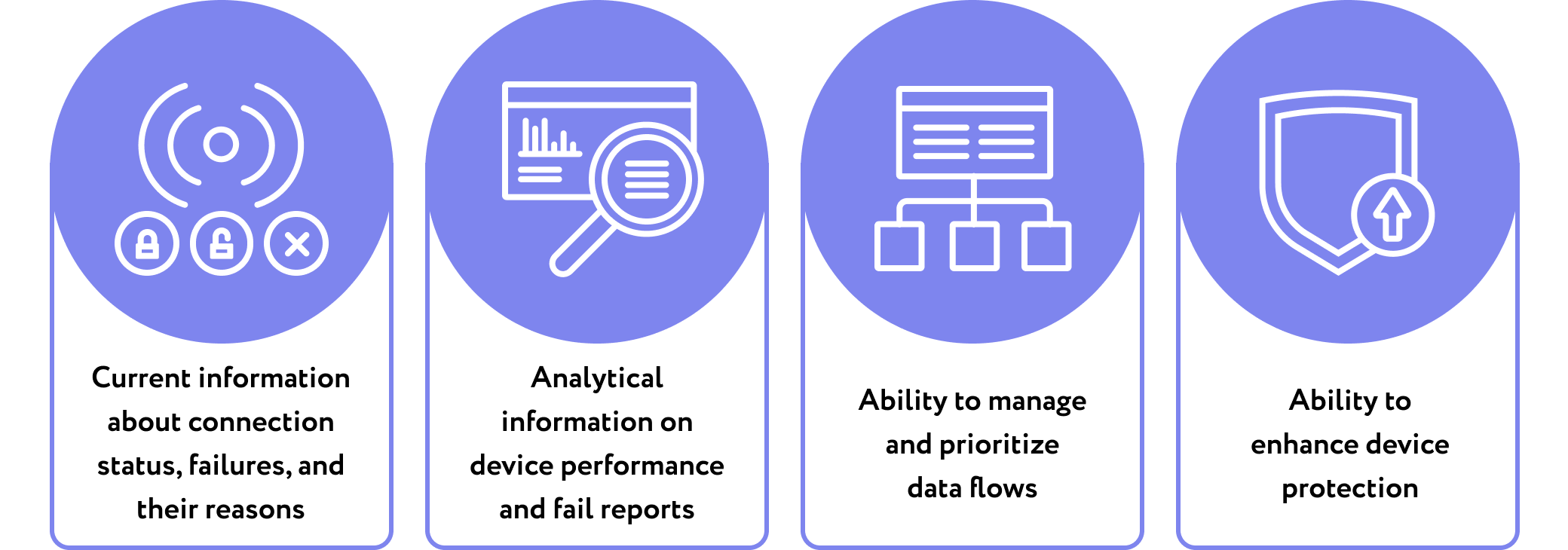
While preparing such a system, it is urgent to make management flexible and scalable to add new devices and change monitoring parameters by request.
Further Shield the Devices To Be Considered During IoT Deployment
Many “things” are vulnerable to attacks by default, especially when it comes to legacy. A comprehensive IoT connectivity creates a large attack surface allowing it to get into the central storage by breaching an end-point device. It empowers the overall system when devices are designed with built-in security measures, but additional measures are never superfluous. That’s why creating strong security policies with clearly defined goals is crucial here.
Generally, IoT cybersecurity involves strengthening at the following levels:
-
Physical devices against illegal access
-
Applications at the transportation layer and HTTPS
-
Network security via corresponding protocols
-
Sideband control
To protect assets managed by a central control unit, consider network segmentation, establish regular updates, and empower access control. From experience, we advise involving a separate security team to cooperate with the development team for the strongest security measures. Together, it should be decided on how to distribute access levels, the amount and location of firewalls, the principle for grouping devices to monitor traffic, and so on.
Final Thoughts on IoT Deployment
IoT deployment creates specific issues mostly through distributed and legacy devices that should be set up to maintain the highest reliability and performance. To alleviate deployment-related risks as well as increase the predictability of the system operation, we recommend considering the following opportunities.
-
Profound strategic planning for IoT deployment provides for detailed risk assessment, security enhancement, and investment justification.
-
Pay special attention to the set-up and maintenance of edge infrastructure. Build a robust device network management app for predictive maintenance opportunities.
-
Security breaches happen rarely enough, but the consequences are catastrophic. That’s why it is worth considering strict security policies and involving a specialized team to implement security.
-
Device interoperability helps with Proof of Concept, expanding use cases, and setting up connections for legacy. Avoid any aspect where you are forced to rely on one vendor.















